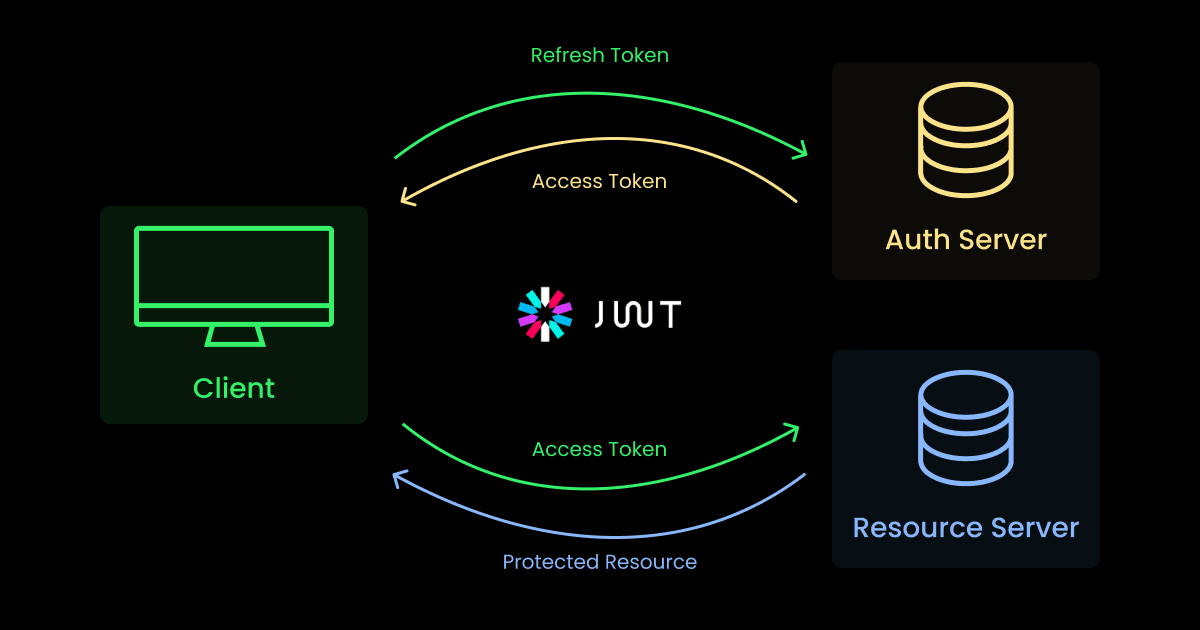
How to allow users to connect from multiple devices using refresh tokens
Allowing users to connect from multiple devices using refresh tokens is an effective way to manage sessions, enhancing security and providing a smooth user experience. Here are the basic steps to set up a system using refresh tokens:
1. Create Access Tokens and Refresh Tokens
When the user logs in successfully, the system generates two types of tokens:
- Access Token: Used to authenticate users and allow access to resources or APIs. The life of this token is usually short (e.g. 15 minutes).
- Refresh Token: Used to obtain a new access token when the current token expires without requiring a user to log in again. Refresh tokens have a longer lifetime (e.g. 7 days or longer).
2. Token Storage
Store access tokens and refresh tokens at the client-side (e.g. in LocalStorage, SessionStorages, or cookies with necessary security settings such as HttpOnly, Secure). Ensure that the refresh token is securely stored and only transmitted via HTTPS to prevent exposure.
3. Using and Managing Access Tokens
Access tokens are used in every request that a user sends to the server for authentication. When the access token expires, the client will use the refresh token supplied in the request to request a new access Token.
4. Refresh Access Token
When the server receives a request with a refresh token, it checks the validity of the token. If valid, the server will issue a new access token and send it back to the client. In some cases, the server may also decide to issue a new token refresh.
5. Manage multi-device sessions
To support users connecting from multiple devices:
- Release separate refresh tokens for each device when the user logs in.
- Save these refresh tokens in the server's database with user and device association information.
- When a refresh token is used to obtain a new access token, update the relevant information in the database (e.g. last usage time).
6. Processing Export and Revoke Tokens
When the user logs out of the device, make sure to remove the refresh token from the database and also the token stored on the client-side. For refresh tokens revoked (for example, for security reasons), the server must also reject any authentication requests using the token.
Using refresh tokens requires careful design and management to ensure the security of information and user experience. Don't forget to check and adhere to security best practices for your system!